noESOTERICStarting the new day with enthusiasm for problem-solving and life's simple pleasures, showing that the world of computers and technology is far from esoteric.

New Kid on the Block: Silver SAML
Hot off the press, cybersecurity mavens have unveiled a new shenanigan in the cyber realm, dubbed "Silver SAML." This fresh technique outfoxes even the staunch defenses set against its notorious predecessor, Golden SAML, posing a sophisticated threat to identity systems.
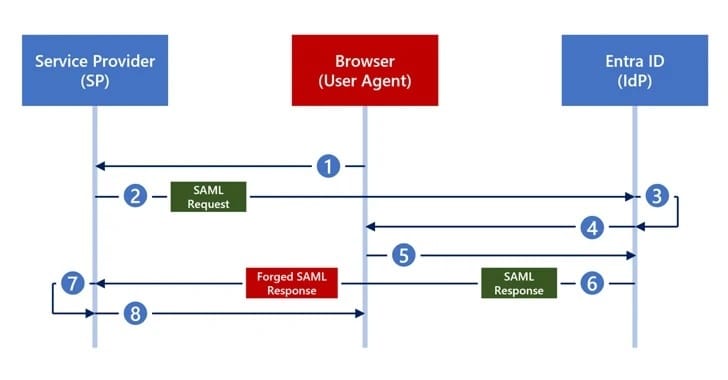
Imagine Golden SAML as the seasoned trickster of authentication hijinks, allowing bad actors to masquerade as just about anyone within an organization. Now, enter Silver SAML, the new ruse on the block, capable of launching assaults from identity providers like Entra ID against apps that lean on them for authentication, say, your trusty Salesforce.
But here's the kicker – Silver SAML doesn't need to meddle with Active Directory Federation Services (AD FS) or nab any SAML token signing certificates. It's slick and operates under the radar, with Microsoft even weighing in to say they're keeping an eye out, although they're not hitting the panic button just yet.

For the tech-savvy enterprises out there, the clarion call is to stick to Entra ID's self-signed certificates for SAML signing, steering clear of external certificates' potential pitfalls. And for those who like to keep tabs, Semperis's new proof-of-concept, SilverSAMLForger, is your new best friend for crafting custom SAML responses.

Wi-Fi Woes: Android and Linux in the Hot Seat
Beware, Android and Linux users! Your device's Wi-Fi might be wooing you into a hacker's trap. Cybersecurity sleuths have unearthed two gnarly vulnerabilities that could let bad actors set up sinister Wi-Fi doppelgängers or crash your trusted network parties without an invite.
The culprits? Two flaws tagged as CVE-2023-52160 and CVE-2023-52161. They lurk in the open-source Wi-Fi wardrobes of not just Android and Linux, but ChromeOS too. The trickery involves luring devices to connect to malevolent mirror networks or letting hackers hop onto secure Wi-Fi without the secret handshake (read: password).
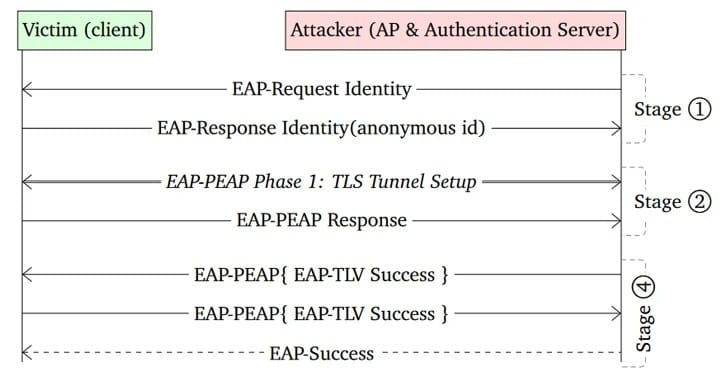
CVE-2023-52161 is a sneaky gatecrasher allowing uninvited access to secure Wi-Fi networks, particularly menacing for IWD versions 2.12 and lower. CVE-2023-52160, the more widespread worry, targets wpa_supplicant versions 2.10 and under, the go-to for Android's Wi-Fi dealings.
While patches are parachuting in for various platforms, Android folks need to be on high alert and tweak their Wi-Fi settings to dodge this digital deceit.

CISA Under Siege: A Cybersecurity Wake-Up Call
In a startling revelation, CISA, the cyber guardian angel of U.S. infrastructure, fell prey to hackers this February. The culprits exploited weaknesses in Ivanti products, prompting an urgent system shutdown by the agency.
A Bit About CISA: This cybersecurity sentinel, born out of the rising digital threats and infrastructure vulnerabilities, has been the nation's cyber shield since 2018. Its mission? To fortify the U.S.'s digital defenses and shield its critical infrastructure from nefarious cyber activities.
The Breach Breakdown: Using Ivanti's chinks in the armor, hackers infiltrated two CISA systems tied intimately to America's infrastructure security. Though the breach was contained to these systems, the incident sends shockwaves across the cybersecurity community, emphasizing that no entity, however fortified, is immune to cyberattacks.
The Irony: Before the breach, CISA had flagged Ivanti's vulnerabilities, urging U.S. government agencies to sever connections with the compromised software. Yet, it was these very vulnerabilities that bit back, showcasing the relentless persistence of cyber adversaries.
While the operational gears of CISA remain unhampered, the incident is a stark reminder of the perpetual cat-and-mouse game in cybersecurity. It underlines the critical need for robust incident response plans and a relentless commitment to digital vigilance.





