Happy New Year and welcome to 2024! As we kick off a fresh start, let's dive into some of the most intriguing stories that are shaping our digital landscape.
First up, we navigate the treacherous waters of cyber threats, where UK's Radioactive Waste Management company narrowly escaped a digital disaster, highlighting the increasing sophistication of cyber-attacks. Then, we shift gears to the realm of cryptocurrencies, where Orbit Chain's bridge became the latest victim of a high-stakes cyber heist, reminding us of the fragility of digital assets.
But it's not all about digital doom and gloom. We explore the paradoxical world of ethical hacking, where white-hat heroes use their skills to fortify our digital defenses against their nefarious counterparts. It's a reminder that in the shadowy alleys of the internet, there are still knights in shining armor.
So let's explore these captivating stories that are reshaping our understanding of the digital frontier. Here's to a year of staying informed and staying secure!
Cybersecurity Alert: UK's Nuclear Waste Company Under Attack
In a digital age twist, Radioactive Waste Management (RWM), the developer of Britain's £50bn underground nuclear waste store, reported a failed cyber-attack via LinkedIn. RWM, part of the newly merged Nuclear Waste Services (NWS), which oversees several nuclear projects, detected attempts to exploit the company's personnel changes for unauthorized access.
Digital Defense Holds Strong Despite these cyber incidents, NWS's defenses held up without any material impact. However, this highlights a growing trend of using social media, particularly LinkedIn, as a hacker's playground. Tactics range from fake accounts and phishing to credential theft, aimed at extracting sensitive information or gaining unauthorized access.
The Geological Disposal Facility (GDF) Project Amidst these security concerns, the GDF project, expected to cost up to £53bn, marches on. It's a massive undertaking, aiming to safely house Britain's highly radioactive waste in an extensive network of subterranean tunnels and vaults. While facing local opposition, the government continues its search for a suitable location, with sites in Cumbria and on the Lincolnshire coast under consideration.
The Broader Picture NWS remains vigilant, acknowledging the constant cyber threats to nationally significant sectors. Despite no disruption to business or site operations, the company continues to enhance its cybersecurity measures. This incident serves as a reminder of the evolving nature of digital threats, especially in critical industries like nuclear waste management.
Orbit Chain Bridge Breach: A $82M Cyber Heist
In a startling breach of digital security, the cross-chain project Orbit Chain suffered a massive hack, leading to an $82 million loss. The attack centered on the protocol's bridge, a key component facilitating asset transfers across over 15 public blockchain networks, including giants like Ethereum, Polygon, and Ripple.
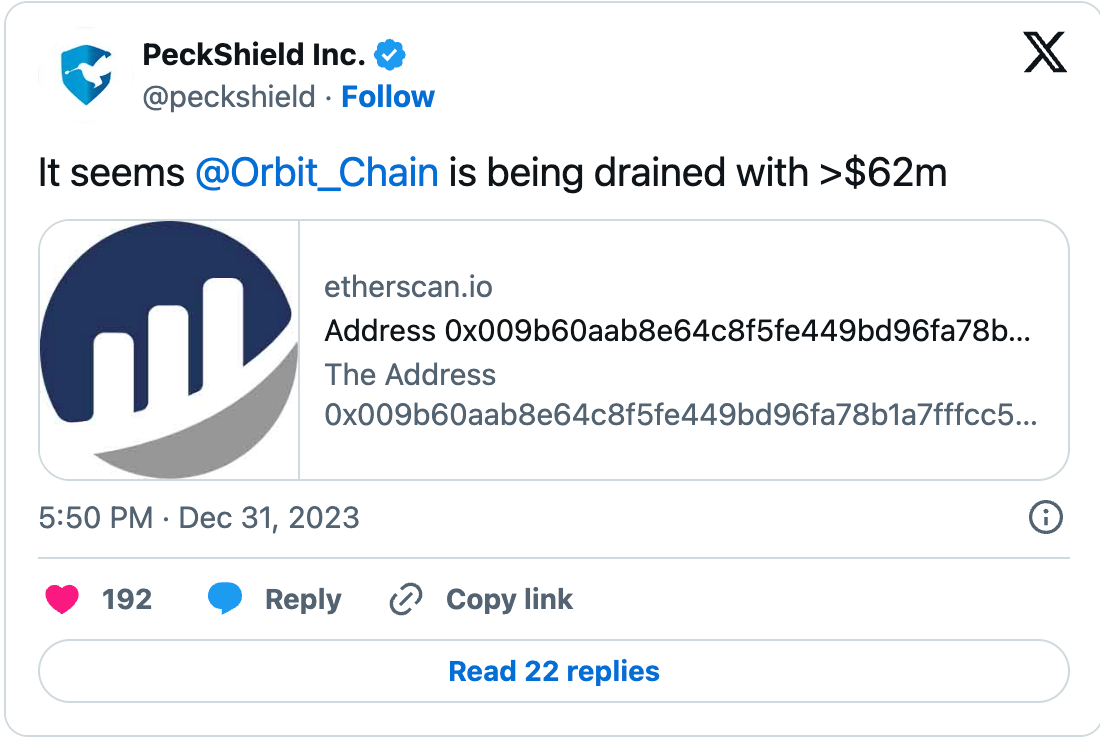
A Staggering Loss PeckShield, a blockchain security platform, was first to spot the breach, witnessing $62 million worth of cryptocurrencies being drained before escalating further. Detailed on-chain data revealed the attacker's haul: 30 million USDT, 10 million DAI, 231 wrapped BTC, and 9,500 ETH, totaling $21.5 million.
DeFi's Vulnerability Exposed This incident adds to the growing list of decentralized finance (DeFi) platforms falling prey to cybercriminals. Similar to recent attacks on Heco Bridge and KyberSwap, the Orbit Chain exploit underscores the inherent risks in the burgeoning DeFi sector.
Market Reaction: ORC Dips Following the breach, Orbit Chain's native cryptocurrency, ORC, experienced a 5% decline, trading at $0.0685. Remarkably, despite the heist, the protocol's total value locked (TVL) remains stable at $151.9 million.

This breach serves as a stark reminder of the critical need for fortified security measures in the DeFi ecosystem, as hackers continue to target these platforms with increasing sophistication.

The Paradox of Ethical Hacking
In the shadowy world of cyber threats, ethical hacking emerges as a beacon of hope. Often misunderstood due to its portrayal in pop culture as a nefarious activity, ethical hacking defies these stereotypes by serving as a crucial tool in cybersecurity.
White Hats to the Rescue Ethical hackers, or white hat hackers, are the digital knights in shining armor. Authorized to breach systems, they mimic black hat hackers' strategies to find and fix vulnerabilities. Their work is essential in a world where their counterparts, the black hat hackers, exploit these same weaknesses for harmful purposes.
Proactive Protection The goal of ethical hacking is straightforward: identify potential threats to prevent cyber attacks. Through methods like penetration testing and vulnerability assessments, ethical hackers simulate attacks to discover weaknesses in digital defenses. This proactive approach is critical in safeguarding sensitive data and maintaining system integrity.
Staying Ahead in a Digital Arms Race The digital landscape is ever-evolving, and so are the tactics of cybercriminals. Ethical hackers continuously adapt, learning new strategies to stay ahead of emerging threats. This commitment to continuous education and evolution underscores the dynamic nature of ethical hacking.
A Career in Defense With rising cyber threats, the demand for skilled ethical hackers is growing. Gaining certifications like Certified Ethical Hacker (CEH) is a pathway into this field, where one can make a significant impact in protecting digital infrastructures.
Navigating the Ethical Maze Despite their critical role, ethical hackers often walk a tightrope of legal and ethical boundaries. Their actions must remain within authorized testing limits to avoid legal repercussions. This balance is a constant challenge in their mission to protect the digital world.
In summary, ethical hacking is not just about breaking into systems; it's about fortifying them against those who seek to do harm. It's a field of paradoxes but one that stands as a vital guard against the ever-growing cyber threats.
