Good Morning, Cyber Warriors!
Welcome to today's edition of our cybersecurity newsletter, where we dive deep into the digital trenches to bring you the latest updates from the cyber front. Today's briefing is packed with stories that remind us of the ever-evolving landscape of digital security and the continuous battle between privacy, security, and the ingenious methods of cyber adversaries.
First up, we dissect Google's recent $5 billion settlement in a privacy lawsuit, a tale that reveals the sometimes murky waters of online privacy and the giant's misstep with its 'Incognito Mode'.
Then, we shift gears to a more technical realm, exploring a new variant of DLL search order hijacking that's outsmarting Windows 10 and 11 protections. It's a stark reminder of the persistence of cyber threats and the importance of staying ahead in the cybersecurity arms race.
Our third story introduces the Terrapin flaw, a new vulnerability in the SSH protocol that's causing ripples across the digital world. This intricate exploit shows how even the most secure communication protocols aren't immune to the cunning of cybercriminals.
Finally, we delve into the menacing emergence of JinxLoader, a new malware loader that's adding complexity to the already intricate web of digital threats. It's a reminder of the ongoing innovation in cyberattack methods and the need for constant vigilance.
Google's $5 Billion Incognito Oops
Google's "Incognito Mode" wasn't as private as users thought, and it's costing the tech giant a pretty penny. In a recent legal battle, Google agreed to settle a lawsuit alleging it tracked users' surfing activities in "Incognito Mode". The lawsuit, filed in June 2020, sought a whopping $5 billion, accusing Google of violating federal wiretap laws through Google Analytics.
Not-So-Incognito After All
The crux of the issue? Users thought they were under a cloak of digital invisibility, but Google's data collection told a different story. Even in private browsing, Google could still track user activities, thanks to advertising technologies and analytics APIs.
The Legal Tug-of-War: Google tried to dismiss the lawsuit, highlighting its warning to users about potential visibility of their activities. However, U.S. District Judge Yvonne Gonzalez Rogers wasn't convinced, stating that Google never explicitly informed users about data collection in incognito mode.
Zoom out: This settlement highlights a growing concern over digital privacy and the responsibilities of tech companies in safeguarding user information. It's a reminder that "private" browsing might not be as private as we think.

Windows Security Gets a Curveball
Windows 10 and 11 users, it's time to up your cybersecurity game! A new variant of DLL (dynamic link library) search order hijacking is challenging the security of these Microsoft operating systems. Security Joes, a cybersecurity firm, shared this discovery with The Hacker News, revealing that the technique could allow threat actors to bypass security mechanisms and execute malicious code.
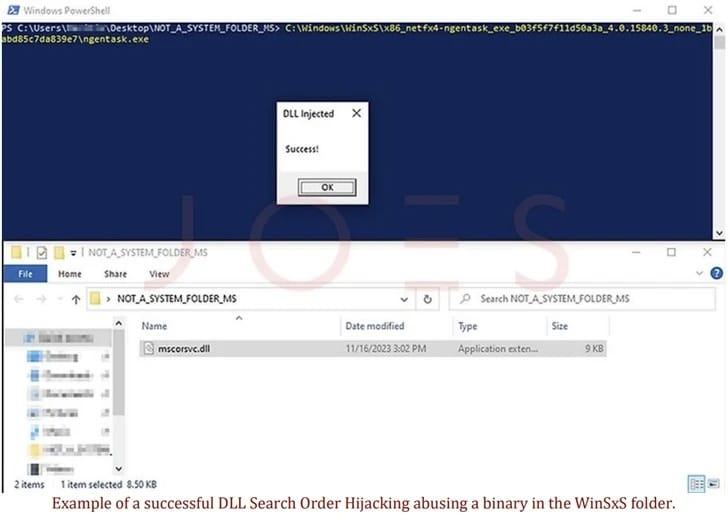
Sneaky Technique, Big Risks
This approach utilizes the WinSxS folder, a crucial component for Windows updates and customization. Attackers place malicious DLLs, named after legitimate ones, in non-standard directories, tricking the system into executing these rogue libraries. It's like a digital sleight of hand, exploiting a gap in how Windows applications load external libraries.
Technical Know-How: The attack focuses on vulnerable binaries in the WinSxS folder, combining them with malicious DLLs placed in actor-controlled directories. This method is subtle yet effective, triggering the execution of the DLL's contents without copying the executable.
Be Alert: Security Joes warns that more binaries might be at risk, urging organizations to monitor parent-child process relationships and activities in the WinSxS folder. It's a call to action for tighter security measures and heightened vigilance in the digital space.
SSH Security Compromised: The Terrapin Flaw
The world of cybersecurity is on high alert as researchers from Ruhr University Bochum reveal a new vulnerability in the Secure Shell (SSH) protocol, dubbed "Terrapin" (CVE-2023-48795). This flaw, with a moderate severity score of 5.9, represents the first practically exploitable prefix truncation attack, capable of downgrading an SSH connection's security.
A Chink in the Armor
SSH, a cornerstone in secure computer communication, is now facing a significant threat. The exploit hinges on manipulating the handshake process, where an attacker can remove messages sent by the client or server without detection.
The Technical Breakdown: The attack is executed by an adversary-in-the-middle (AitM), who intercepts and modifies TCP/IP traffic. It specifically targets SSH extension negotiation, potentially leading to weaker client authentication algorithms and disabled keystroke timing attack countermeasures.
Widespread Impact: A multitude of SSH implementations, including popular ones like OpenSSH, PuTTY, and FileZilla, are affected. This vulnerability poses a particularly acute risk for large networks with privileged data access.
Patch and Protect: The discovery has led to urgent patch releases from affected maintainers. Yet, the risk remains unless both clients and servers are updated, highlighting the need for comprehensive infrastructure assessment and immediate mitigation efforts.

JinxLoader: A New Menace in Cybersecurity
The cyber world is facing a new threat: JinxLoader, a Go-based malware loader, is making waves by delivering dangerous payloads like Formbook and XLoader. Cybersecurity giants Palo Alto Networks Unit 42 and Symantec have shed light on this emerging threat, which cleverly uses phishing attacks for its dirty work.

A Lethal Phishing Expedition
JinxLoader, drawing inspiration from the League of Legends character Jinx, starts its attack with seemingly innocent phishing emails. These emails, masquerading as communications from Abu Dhabi National Oil Company, trick recipients into opening RAR archives that unleash the JinxLoader executable. This acts as a gateway for more sinister malware.
Priced for Cybercrime: First advertised on hackforums[.]net, JinxLoader's accessibility for $60 a month, $120 a year, or $200 for a lifetime, makes it a go-to tool for cybercriminals.
Expanding Threat Landscape: The rise of JinxLoader coincides with a spike in infections from other loader malware families like Rugmi, DarkGate, and PikaBot. Notably, TA544 (aka Narwal Spider) is leveraging new loader malware variants to deploy even more dangerous threats.
Malware Market Booming: The malware market is growing, with new entrants like Vortex Stealer making their mark. This malware family is known for stealing a wide range of sensitive information, from browser data to Discord tokens.
