Good Evening, Cyber Guardians! As the sun sets, let's reflect on today's cybersecurity landscape with a concise roundup of today's articles. We began with the urgent CISA directive, a clear call to action for federal agencies to patch critical vulnerabilities, a move reflecting the seriousness of cyber threats in our government's infrastructure.
Next, we delved into the world of iPhone security with the iShutdown method, a game-changer in detecting spyware like Pegasus. This innovative approach underscores the evolving nature of cyber threats and the ingenuity required to counter them.
Finally, we explored a structured guide for cybersecurity beginners, highlighting the importance of a guided approach in a field as complex and dynamic as cybersecurity. This piece serves as a beacon for aspiring cyber professionals, illuminating the path to mastery.
As night falls, these articles serve as a reminder of the constant vigilance and continuous learning required in the ever-shifting seas of cybersecurity. Stay curious, stay informed, and most importantly, stay secure.

Urgent Cybersecurity Action Required by Federal Agencies
In a decisive move to protect national cybersecurity, the Cybersecurity and Infrastructure Security Agency (CISA) has issued an emergency directive, mandating federal agencies to urgently address two significant vulnerabilities discovered by software firm Ivanti.
Immediate Threat Neutralization
The identified vulnerabilities, CVE-2023-46805 and CVE-2024-21887, allow attackers extensive network access, including data exfiltration and persistent system access.
Ivanti's products, particularly Ivanti Connect Secure and Ivanti Policy Secure, are at the center of this security scare, with vulnerabilities enabling authentication bypass and command injection.
Agencies have been instructed to implement Ivanti’s mitigation measures immediately, run the External Integrity Checker Tool, and report any signs of compromise.
CISA's Stance: CISA Director Jen Easterly emphasizes the critical nature of these vulnerabilities, urging not only federal agencies but all organizations using Ivanti products to take swift action. The directive reflects CISA's commitment to safeguarding federal civilian enterprise and its systems.
Broader Impact: While federal exposure seems limited, with around 15 agencies using the affected products, the private sector faces a larger threat, with over 1,700 organizations reportedly impacted. CISA's emergency directive is also a clarion call for the private sector to address these vulnerabilities.
Next Steps: Agencies are required to provide a complete inventory of Ivanti products on their networks within a week and CISA will report the overall status to the White House and other key departments by June 1.
This directive highlights the ongoing vigilance and proactive measures needed in the ever-evolving cybersecurity landscape.

A groundbreaking discovery in cybersecurity has emerged with Kaspersky's development of "iShutdown," a method capable of detecting stealthy spyware like Pegasus on iOS devices.
Efficient Spyware Detection
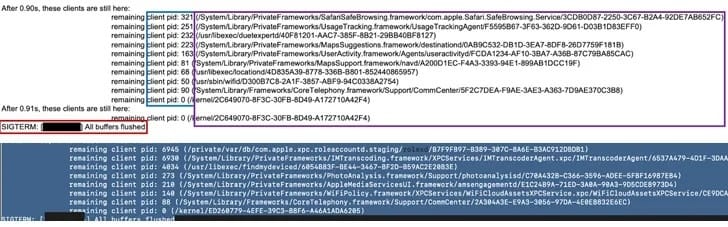
iShutdown targets a system log file, "Shutdown.log," which records every reboot and its environment on iPhones.
Unlike complex methods like forensic imaging, iShutdown simply analyzes this log for traces of spyware activity, such as reboot delays caused by persistent spyware processes.
This approach successfully identified activities related to infamous spywares like Pegasus, Reign, and Predator, hinting at their operational patterns.
Kaspersky has also published a collection of Python scripts to extract, analyze, and parse the Shutdown.log in order to fetch the reboot stats, such as first reboot, last reboot, and the number of reboots per month.
How it Works: iShutdown looks for unusual entries in the Shutdown.log, especially delays in reboot processes caused by spyware. These delays and specific filesystem paths used by spywares act as indicators of compromise.
User's Role: Effectiveness of iShutdown is partially dependent on the frequency of device reboots by the user.
Tool Availability: Kaspersky has released Python scripts for the public, enabling easy analysis of Shutdown.log files for potential spyware indicators.
Forensic Value: The Shutdown.log can retain data for years, making it a crucial forensic resource for long-term analysis.
Broader Cybersecurity Context: This method's unveiling coincides with revelations of macOS-targeting information stealers adapting to bypass Apple's XProtect. It highlights the ongoing challenge of keeping up with evolving malware and the limitations of signature-based detection methods.
iShutdown represents a significant leap in efficiently and effectively identifying deeply hidden threats on iOS devices, marking a key advancement in the ongoing battle against sophisticated cyber threats.

Kickstarting Your Cybersecurity Career: A Guide for Beginners
Embarking on a cybersecurity journey can seem overwhelming, but with the right approach and resources, beginners can navigate this dynamic field with confidence.
Essential Steps to Start in Cybersecurity
1. Understanding the NIST-NICE Framework: This framework provides a structured approach to cybersecurity roles, categorizing them into seven categories like Analyze, Protect and Defend, Investigate, etc. It's a valuable roadmap for career progression.
2. Networking with Industry Experts: Interacting with experienced professionals is crucial. Attend cybersecurity events like DEF CON, OWASP meetings, and BSides to engage with the community, participate in workshops, and build valuable connections.
3. Participate in CTF Challenges and Hackathons: Engaging in Capture The Flag challenges and hackathons is an effective way to apply cybersecurity concepts in practical scenarios. These events align with various areas of the NIST-NICE framework, like Analyze, Protect and Defend, and Investigate.
4. Join Bug Bounty Campaigns: Participating in bug bounty programs from companies like Google, Apple, or through platforms like Bugcrowd and Hackerone is an excellent way to gain real-world experience while contributing to the security of major systems.
5. Utilize Practical-Led Training Resources: Engage with platforms offering practical cybersecurity training, like OverTheWire, Root Me, PortSwigger Academy, and others. These resources offer a range of challenges from basic to advanced levels.
6. Leverage Social Media and Forums: Platforms like LinkedIn, Discord, and specialized forums like Reddit’s Cybersecurity Communities, Wilders Security Forums, and Bleeping Computer can be instrumental in finding mentors and staying updated on industry trends.
7. Utilize Free Tools: Familiarize yourself with tools like Wireshark, OWASP ZAP, Metasploit Community Edition, Snort, OpenVAS, and Kali Linux. These tools offer practical experience and are accompanied by extensive documentation and community support.
Key Takeaways for Beginners
Structured Learning: While curiosity is crucial, structured learning paths like the NIST-NICE framework provide a clear direction.
Community Interaction: Building relationships with professionals and participating in real-time events are pivotal for growth.
Practical Experience: Hands-on experience through CTFs, bug bounties, and practical-led training is essential.
Mentorship and Resources: Utilize online communities and free tools to supplement your learning and find mentorship.
Embarking on a cybersecurity career requires a blend of structured learning, practical experience, and community engagement. With these steps and resources, beginners can navigate their path in this ever-evolving field with greater confidence and clarity.




