Good Evening Brew-tiful People! Welcome to 2024, where our digital landscape is bustling with more twists and turns than a Sherlock Holmes novel.
First up, we have a tale that sounds straight out of a spy thriller - SMS spoofing. Imagine sending texts without even touching your phone; sounds cool unless you're like John from Fort Myers, who's left scratching his head over mysterious texts.
Moving on, we take a dive into the murky waters of Structured Format Injection - a hacker's magic trick for turning innocent APIs into their playground.
And for the grand finale, we hop onto the enterprise browser bandwagon, unraveling the mysteries of choosing the perfect guardian for your digital gateway.
So, buckle up, dear readers, as we embark on a journey through the labyrinth of digital security, where each click could be an adventure (or a misadventure). Let's decode the enigma wrapped in a riddle, shall we? 🕵️♂️🔍👾

Beware the API: The Perils of Structured Format Injection
n the ever-evolving landscape of cybersecurity, Structured Format Injection (SFI) emerges as a formidable threat, especially in API security. The crux of the problem lies in the implicit trust developers place in structured data formats like JSON and XML, which are widely used in APIs. These formats, when manipulated, can lead to serious vulnerabilities and unauthorized access.
A Hacker's Playground: Exploiting with SFI
The technique of SFI involves altering the structure of data in transit between systems. This manipulation can range from adding extraneous fields to injecting malicious code. A common scenario involves Server Side Parameter Pollution (SSPP), where endpoints meant for partial data updates are exploited. For instance, an attacker might manipulate a user profile update feature to alter their role from "user" to "admin" in a database, exploiting the auto-binding feature in software frameworks.
Case Study: The JSON Trick
Consider an API where updating a display name is possible through a POST request. An attacker could modify this simple request to include an additional 'admin' role, leveraging the automatic binding of request parameters to internal objects. This results in unauthorized elevation of privileges.
Zooming In: The danger also lies in manipulating Content-Type headers. By sending a JSON object instead of form data, attackers can bypass certain input filters, allowing for more intricate tampering.
The Big Picture
SFI can expose APIs to Broken Object Property Level Authorization vulnerabilities. It's a subtle yet powerful way to "restructure" JSON objects behind the scenes, highlighting the need for rigorous input validation and cautious handling of user data.
Key Takeaway: In the realm of API security, never underestimate the power of data structure manipulation. It's a reminder that in cybersecurity, complacency can be the biggest vulnerability.

The Definitive Guide to Choosing an Enterprise Browser
n the digital age, the browser stands as a critical tool in corporate environments, yet it's also a prime target for cyberattacks. Recognizing this, security teams are increasingly turning to enterprise browsers, a solution specifically tailored to address browser-related security challenges.
This emerging field lacks established best practices, making the selection process for the right enterprise browser complex. LayerX steps in with its comprehensive Enterprise Browser Buyer's Guide, offering an actionable checklist for evaluating potential solutions.
The Browser: A Double-Edged Sword
Serving as the gateway to both sanctioned SaaS applications and potential cyber threats, the browser is a unique point of convergence for cloud environments and endpoints. This dual role makes it vulnerable to a range of attacks, from browser exploits to phishing schemes, and even sophisticated data exfiltration methods.
Essentials of Browser Security
The guide divides browser security into two main aspects: data protection and threat prevention. Data protection involves ensuring sensitive corporate information isn't misused, while threat prevention focuses on countering attacks targeting the browser, user credentials, and exploiting web page technologies.
Choosing the Right Solution
When selecting an enterprise browser, consider factors like deployment methods, architectural differences, user privacy, and threat prioritization. Given the novelty of enterprise browsers, peer advice is scarce, making the guide an invaluable resource.
In-Depth Analysis and Practical Checklist
The guide breaks down browser security into digestible segments, focusing on deployment, user experience, security functionalities, and privacy. Particularly notable is the security function segment, which addresses aspects like attack surface management, Zero Trust Access, SaaS monitoring, protection against malicious web pages, and secure third-party access.
Conclusion: The guide's comprehensive checklist simplifies the evaluation process, enabling an informed decision based on your specific needs.

John from Fort Myers, FL, shares a troubling experience: receiving a text that was a response to a message he never sent. This scenario illustrates a real and growing threat known as SMS spoofing, where cybercriminals send texts from a number that appears to be yours, without needing physical access to your phone.
The Deceptive Art of SMS Spoofing
SMS spoofing manipulates the sender ID, making texts appear to come from a familiar or legitimate number. This technique is not just alarming but also illegal, often used for phishing, identity theft, and fraud. The goal? To trick recipients into revealing personal information, paying fake bills, or damaging reputations.
Vulnerabilities Across Devices
Even devices once deemed secure, like iPhones, are susceptible to this threat. Hackers exploit bugs in iOS, using "interaction-less" bugs to send harmful texts that activate without user interaction. This emphasizes the need for constant vigilance and software updates.


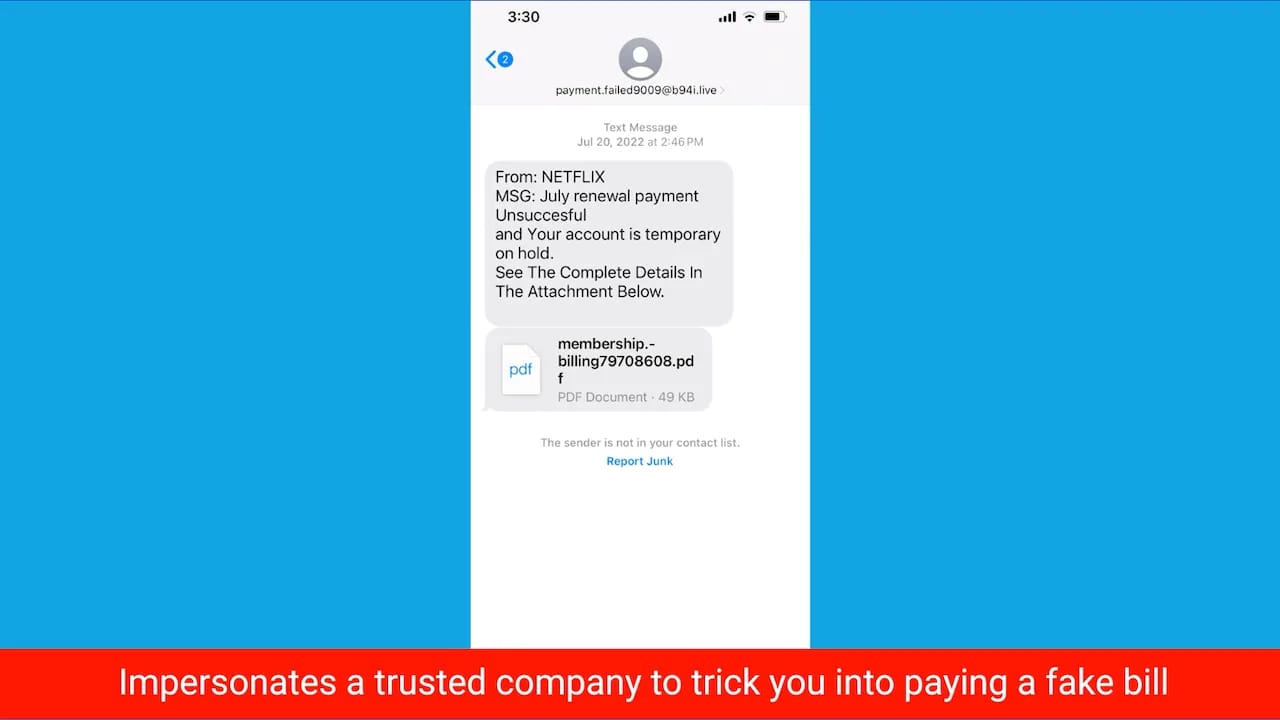


Protecting Yourself Against Spoofing
To safeguard against such attacks, John and others can take several steps:
Install Antivirus Software: Helps detect and prevent malware and phishing attempts.
Regular Updates: Keeping phone software up-to-date to patch security flaws.
Strong, Unique Passwords: Changing passwords regularly and using a password manager for enhanced security.
Two-Factor Authentication: Adds an extra security layer to your accounts.
Alert Your Network: Informing your contacts about potential spoofing to avoid scams.
Professional Assistance: Utilizing identity theft protection services and legal advice for serious cases.
Conclusion: SMS spoofing presents a serious risk, but by taking proactive measures, individuals can significantly reduce their vulnerability to these attacks.
