Good evening, tech wizards! As we wrap up the day, let's take a stroll through the labyrinth of cybersecurity challenges that have unfolded. First up, we explored GitLab's daunting zero-click vulnerability – a stark reminder of the ever-present dangers lurking in our digital ecosystems. Next, we navigated the fortified defenses of Microsoft Teams, witnessing how Microsoft is adapting to the evolving landscape of cyber threats, especially in our communication tools. And finally, we delved into the urgent SharePoint security alert issued by CISA, a critical call to arms against a high-severity vulnerability. These stories not only highlight the relentless pace of cyber warfare but also the resilience and ingenuity in our ongoing battle for digital security. As the evening sets in, let’s stay alert and ready to adapt in this ever-changing cyber world. Stay safe out there!
var codeElement = document.createElement('code');
codeElement.textContent = "Welcome to this edition";
document.body.appendChild(codeElement);Today, he's the CEO of a $2.73 trillion technology giant.
But back in 1993, he was just another middle manager doing Excel demos.
Satya Nadella spent 22 years at Microsoft, climbed up the ladder, and became the CEO. Under his leadership, the Microsoft stock has grown nearly 1,000%.
More importantly, he made Google "dance", almost redefined the AI landscape overnight (by recruiting Sam Altman & other key people from OpenAI), and is currently worth more than $930 million.
Nadella is living proof that there are many ways to succeed.
GitLab's Security Alert: Zero-Click Account Hijacking
In a major cybersecurity update, GitLab has urgently released patches for critical vulnerabilities in both its Community and Enterprise Editions. The most alarming of these is a zero-click exploit, tagged as CVE-2023-7028, with a maximum severity score of 10/10. This flaw allows password resets to be sent to arbitrary, unverified email addresses, potentially leading to account takeovers.
Although two-factor authentication (2FA) provides a layer of protection, the vulnerability remains significant due to the platform's widespread use for hosting sensitive data like proprietary code and API keys. The risk extends to supply chain attacks, where repositories could be compromised by malicious code insertions.
Discovered by security researcher ‘Asterion’, the vulnerability has been present since version 16.1.0, introduced on May 1, 2023. GitLab urges users to update to the latest versions to mitigate this risk. For signs of compromise, GitLab advises checking specific log entries for unusual password reset requests and audit logs for PasswordsController#create entries.
Another critical issue, CVE-2023-5356, scores 9.6/10 and involves the potential abuse of Slack/Mattermost integrations to execute commands as another user.
GitLab also patched other significant vulnerabilities, including a high-severity flaw allowing CODEOWNERS approval bypass (CVE-2023-4812) and an access control issue in Workspaces (CVE-2023-6955).
GitLab's proactive stance in addressing these vulnerabilities reflects the growing emphasis on cybersecurity in the digital age.

Microsoft Teams: Fortified Against Modern Phishing
Microsoft's latest cybersecurity update is a game-changer for Microsoft Teams users. Recognizing the shift in phishing methods from emails to chat messages, especially in popular collaboration tools like Teams, Microsoft has ramped up its defenses with new features in Microsoft 365 Defender.
Why the focus on Teams? The pandemic-induced surge in remote work has made platforms like Teams prime targets for cybercriminals. Attackers are now exploiting chat messages to bypass traditional security measures like Multi-Factor Authentication (MFA).

What's New in Microsoft 365 Defender? The Defender for Office 365 component now includes several robust protections:
Report Suspicious Teams Messages: Users can flag suspicious messages, similar to Outlook's existing feature.
Zero-hour Auto Purge (ZAP) for Teams: This proactive feature scans post-delivery messages and quarantines any with malicious content.
Teams Message Quarantine: Admins can now control and block high-confidence phishing attempts.
Teams Message Entity Panel: A centralized hub for SecOps, consolidating metadata from various chat sources.
Attack Simulation Training: This private preview feature allows organizations to conduct simulated phishing attacks via Teams to raise awareness and preparedness.
These enhancements, part of the Office 365 Plan 2 or Microsoft 365 E5 packages, mark a significant stride in safeguarding collaboration tools against sophisticated cyber threats.

The Cybersecurity and Infrastructure Security Agency (CISA) has raised the alarm on a critical Microsoft SharePoint Server vulnerability, currently tagged in its Known Exploited Vulnerabilities catalog. The flaw, identified as CVE-2023-29357 with a high CVSS score of 9.8, poses a significant privilege escalation risk, potentially granting attackers administrative access.
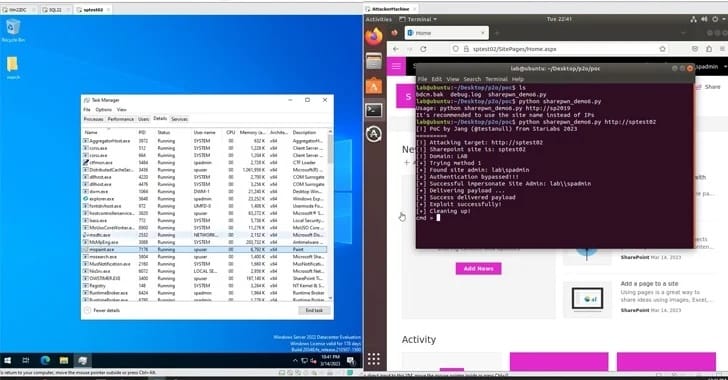
This vulnerability was highlighted when security researcher Nguyễn Tiến Giang of StarLabs SG showcased an exploit at Pwn2Own Vancouver, netting a $100,000 prize. Combining an authentication bypass (CVE-2023–29357) with a code injection bug (CVE-2023-24955), the exploit represents a serious security threat.
Despite Microsoft's release of patches in June 2023, evidence of active exploitation has prompted CISA to urge federal agencies to update their systems by January 31, 2024. The exploit allows attackers to bypass authentication using spoofed JWT tokens, gaining privileges without any user action or existing privileges.
The complexity and severity of CVE-2023–29357, as detailed in Tiến Giang’s report, underscore the critical need for immediate action to patch and protect SharePoint environments against these sophisticated attacks.


