Rise and shine, tech enthusiasts! Grab your coffee, and let's start the day with some eye-opening updates from the digital world. As we navigate through our hyper-connected lives, it's essential to stay informed about the ever-evolving cyber landscape. Today, we've got a lineup that's as intriguing as your first caffeine kick: the cunning FBot targeting cloud services, GitHub's misuse by savvy cybercriminals, and Framework's phishing predicament.
Imagine, as you scroll through your morning emails, a world where even the most trusted platforms become tools for the tech-savvy trickster. It's not just about staying ahead; it's about staying aware. So, let's unravel these digital dramas together.
60 Stories To Learn About Personal Data Security

FBot: A New Python Menace in the Cloud
The cyber realm is abuzz with the latest Python-based hacking tool, FBot, targeting giants like Amazon Web Services, Microsoft Office 365, and PayPal. SentinelOne's recent report highlights FBot's design similarities with the Legion cloud infostealer but notes its unique approach in hijacking cloud, SaaS, and web services.
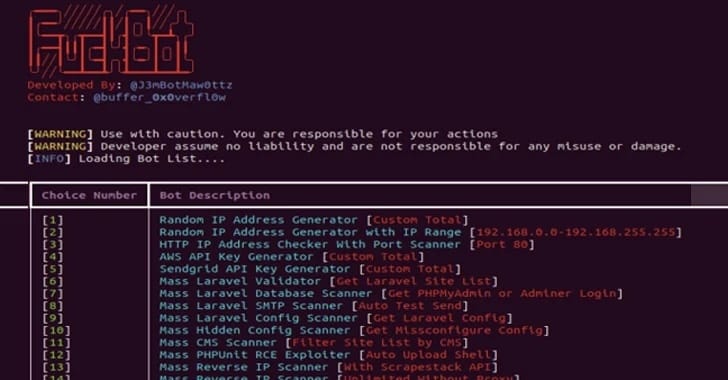
FBot, compact yet potent with 200 KB of code, focuses on credential harvesting for spamming attacks and selling initial access. Balazs Greksza of Ontinue points out its simplistic nature compared to more robust tools like NMAP. FBot's specific functionality in AWS environments is limited to simple checks, indicating that standard security measures like MFA and vigilant IAM can effectively thwart its threats.
Experts like John Bambenek and Emily Phelps suggest bolstering defenses with MFA, regular credential audits, security awareness training, and comprehensive SIEM logging to detect and remediate misuse quickly. The call to action is clear: enhance activity monitoring, maintain updated software, and implement strict access control policies to safeguard against such cyber threats.

GitHub: A Double-Edged Sword in Cybersecurity
GitHub, a cornerstone in IT environments, is increasingly becoming a playground for threat actors. According to Recorded Future, GitHub's widespread use allows adversaries to disguise malicious activities, making detection and attribution challenging. This technique, dubbed "living-off-trusted-sites" (LOTS), is a twist on the "living-off-the-land" strategy, enabling attackers to operate undetected.
A primary concern is the delivery of malicious payloads via GitHub. ReversingLabs highlights the use of secret gists for command-and-control (C2) instructions, a subtle yet effective tactic. More common, however, is GitHub’s role as a dead drop resolver, as seen with malware like Drokbk and ShellBox. GitHub's involvement in data exfiltration is less frequent, likely due to limitations in file size and storage, coupled with the risk of discovery.
Additionally, GitHub Pages are exploited as phishing hosts or traffic redirectors, and repositories sometimes serve as backup C2 channels. This trend is not unique to GitHub; other services like Google Drive, Microsoft OneDrive, and Discord face similar abuses.
The detection of such abuses is complex and requires a mix of strategies tailored to specific environments. Factors like log availability, organizational structure, service usage patterns, and risk tolerance play crucial roles in shaping these strategies.

Framework's Phishing Fiasco: Customer Data Compromised
Framework, a U.S. company known for its repairable laptops, is reeling from a phishing attack on its accounting partner, Keating Consulting. Hackers accessed customer data after duping an employee through social engineering. This breach, affecting Framework's customers, involved personal information like names, email addresses, and outstanding balances.
The attack, executed on January 9th, involved impersonating Framework's CEO to obtain Accounts Receivable details. Framework, established by former Apple and Oculus engineer Nirav Patel, emphasizes the right-to-repair movement. However, this incident highlights the vulnerabilities in digital security, even in tech-savvy companies.
The breach extends beyond Framework, as Keating Consulting serves nearly 300 clients in Silicon Valley. There's uncertainty if other clients, including high-profile companies like GoodRx, Molecule.com, and Udemy, are also affected.
In response, Framework is ramping up security measures, including mandatory phishing training for employees with access to customer information and auditing the practices of finance consultants. While the extent of the breach is still unclear, Framework has notified impacted customers and is working to fortify its defenses against such cyber threats.